This is a semi-automatic penetration testing tool. The current version is mostly used for penetration testing information collection and is updated every week. The ultimate goal is to be a fully automatic penetration testing information collection tool similar to linpeas, and to detect its vulnerabilities.
BUG fix
smb specifies the account to log in to the folder
Interface optimization, program optimization
Generate shellcode and connect
Added WPScan tool
git:
git clone https://github.com/baimao-box/satania.git
After downloading the tool, enter the directory where the tool exists to install
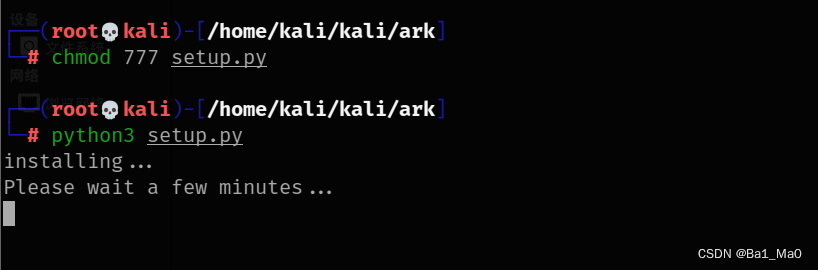
chmod 777 setup.py
python3 setup.py
You need to wait a few minutes, during which you need to manually select something, the default is OK
After the installation is complete, you will be prompted whether to install the searchsploit tool. This tool is very large, so ask here, if the network is good, you can install it
Then directly enter satania to run the tool
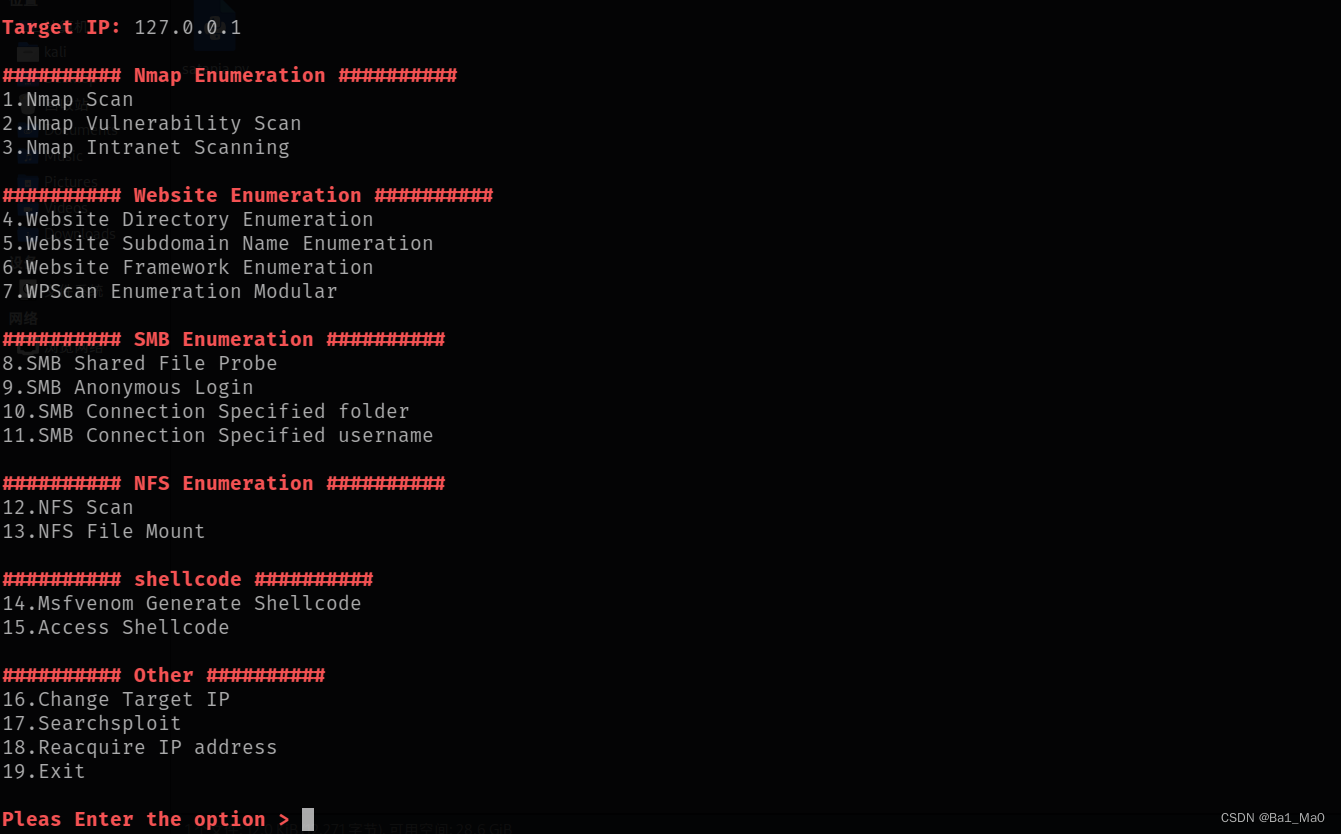
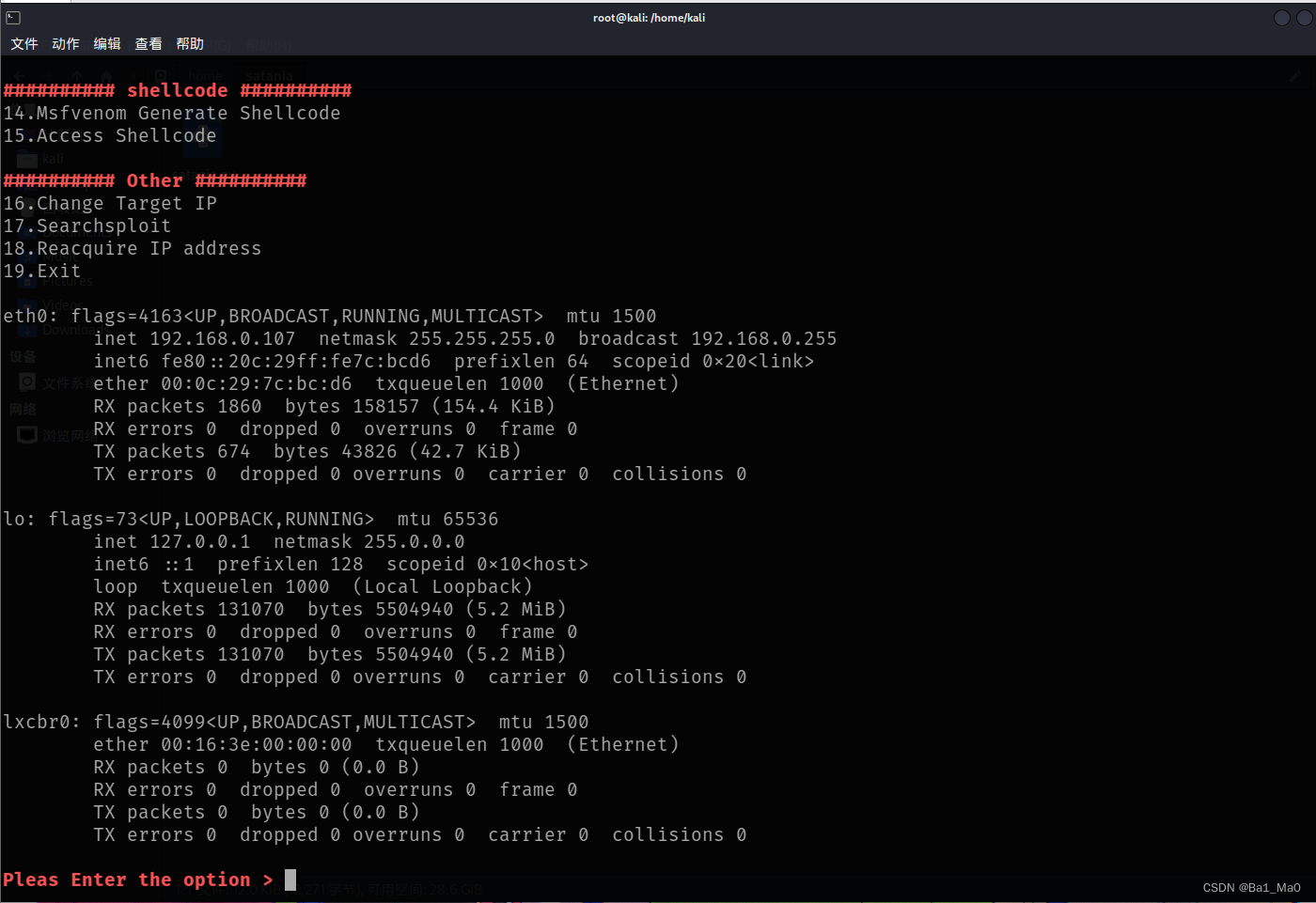
1. nmap enumeration
2. Nmap routine vulnerability scanning
3. nmap intranet live host detection
4. Website root directory file scan
5. Website subdomain enumeration
6. Website frame enumeration
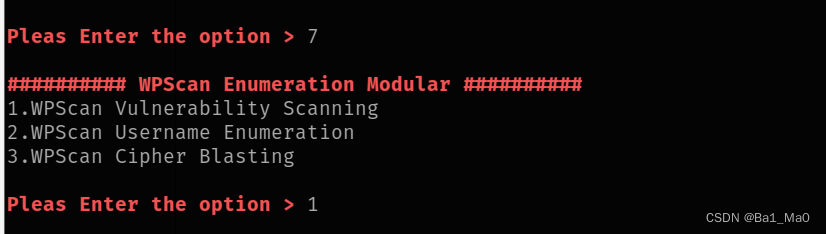
7. wpscan enumeration
1. WPScan Vulnerability Scan
2. WPScan username enumeration
3. WPScan account blasting
8. smb shared directory enumeration
9. Anonymous login
10. smb specified folder login
11. smb specify the user name to log in
12. nfs scan
13. nfs local mount
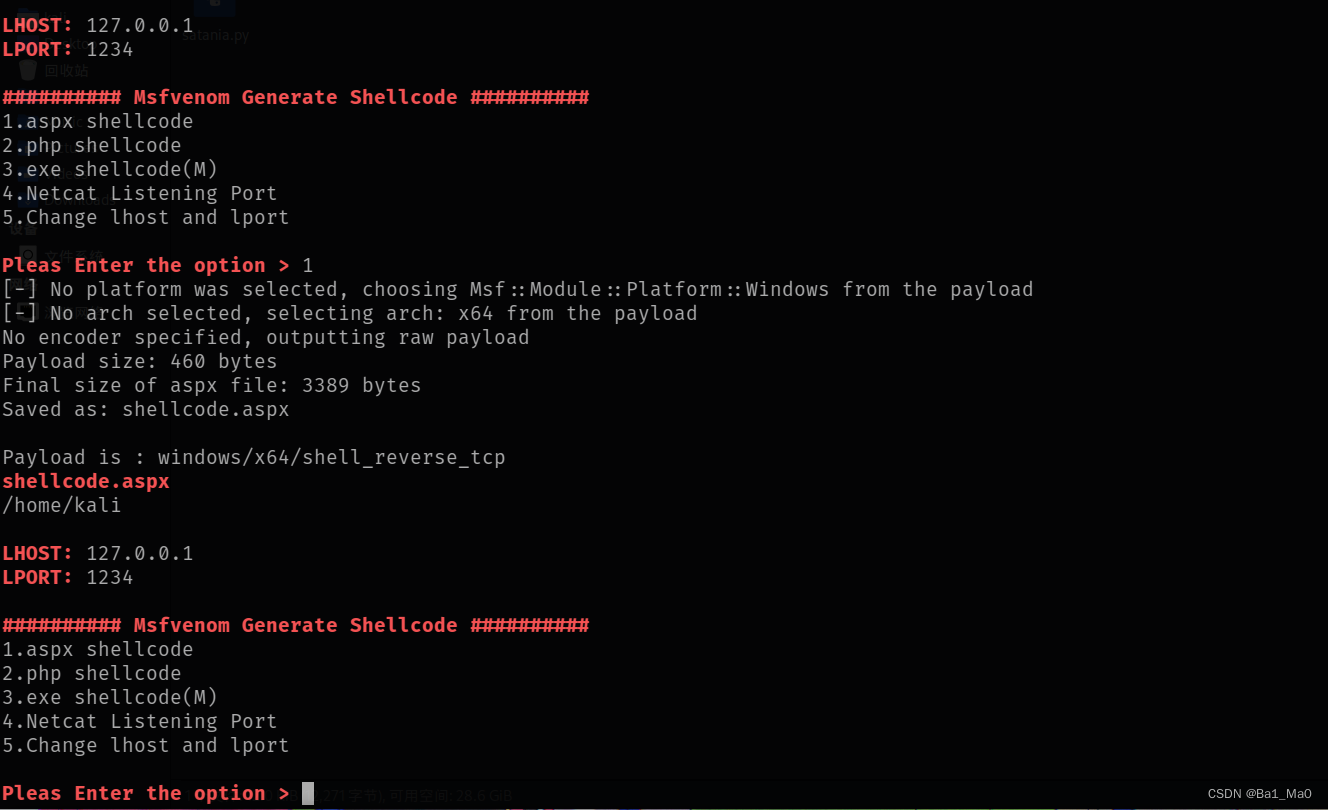
14. msfvenom generates shellcode
1. aspx shellcode
2. php shellcode
3. exe shellcode
4. netcat monitoring
5. Change the local ip and port of the settings
15. Connect the uploaded shellcode
16. Change the target ip
17. searchsploit
18. Re-acquire the local IP
19. Exit
During the execution of the command, the linux command can still be run normally
Updates are as follows:
BUG fix
smb specifies the account to log in to the folder
Interface optimization, program optimization
Generate shellcode and connect
Added WPScan tool
Use the wpscan enumeration module to perform default vulnerability scans
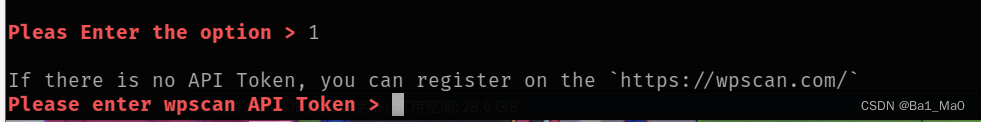
Here you will be asked to enter the api token
When we usually use wpscan, we need to enter the api token for each scan. Using this tool, you can store your api token, and then you don't need to enter it for calls.
Various scans can then be performed
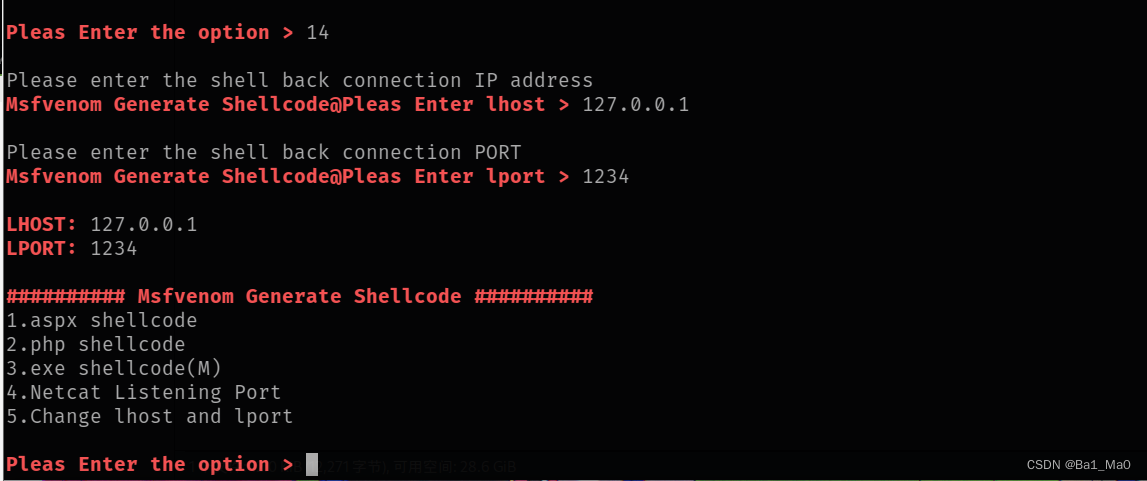
We enter the msfvenom module
The tool will prompt you to enter the local ip and listening port for subsequent shellcode generation, now we generate a shellcode
The tool will enter the file name, the address where it is stored, and the payload used
This update puts the executed linux command below
Keep updating every week