Published as a public Terraform registry module
 Talk and demo on YouTube
Talk and demo on YouTube
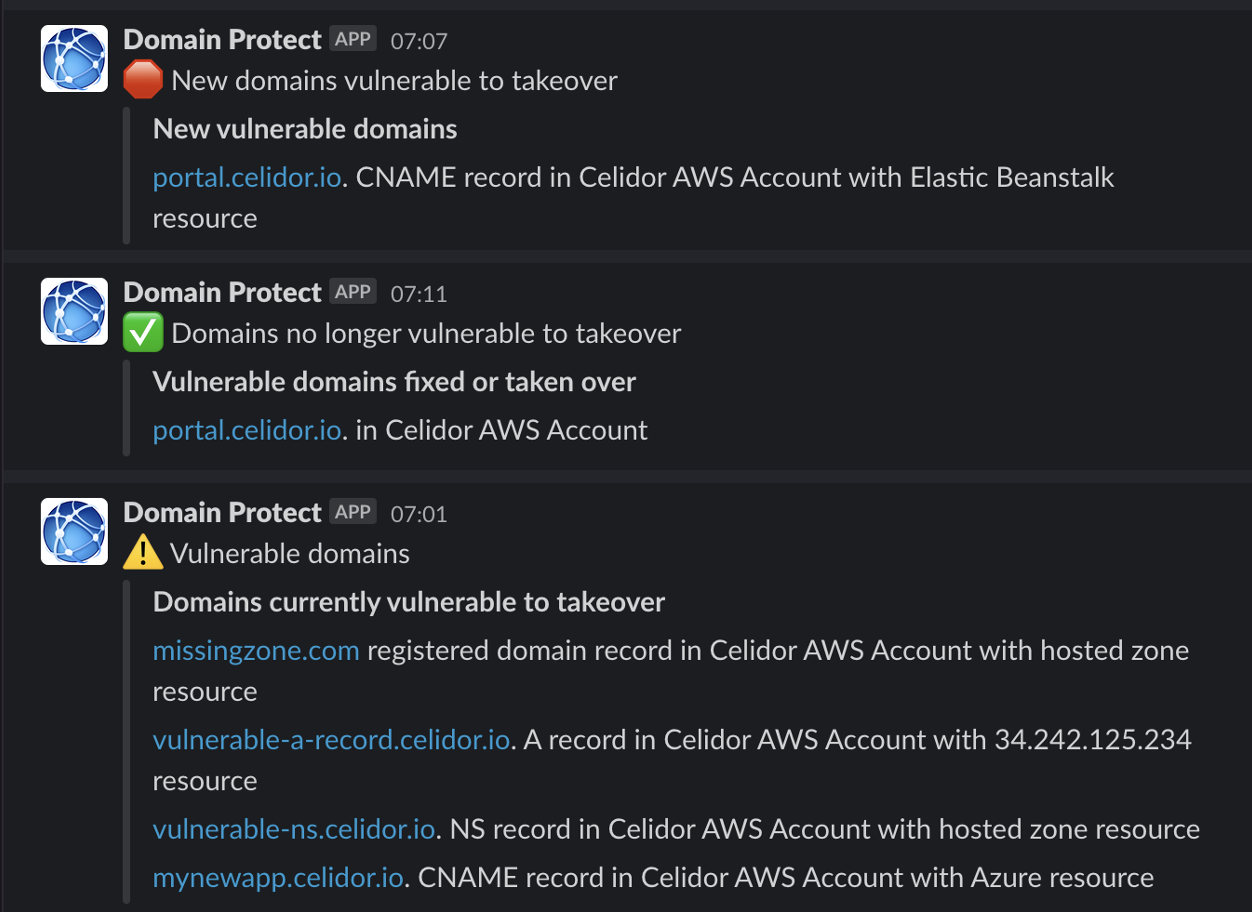
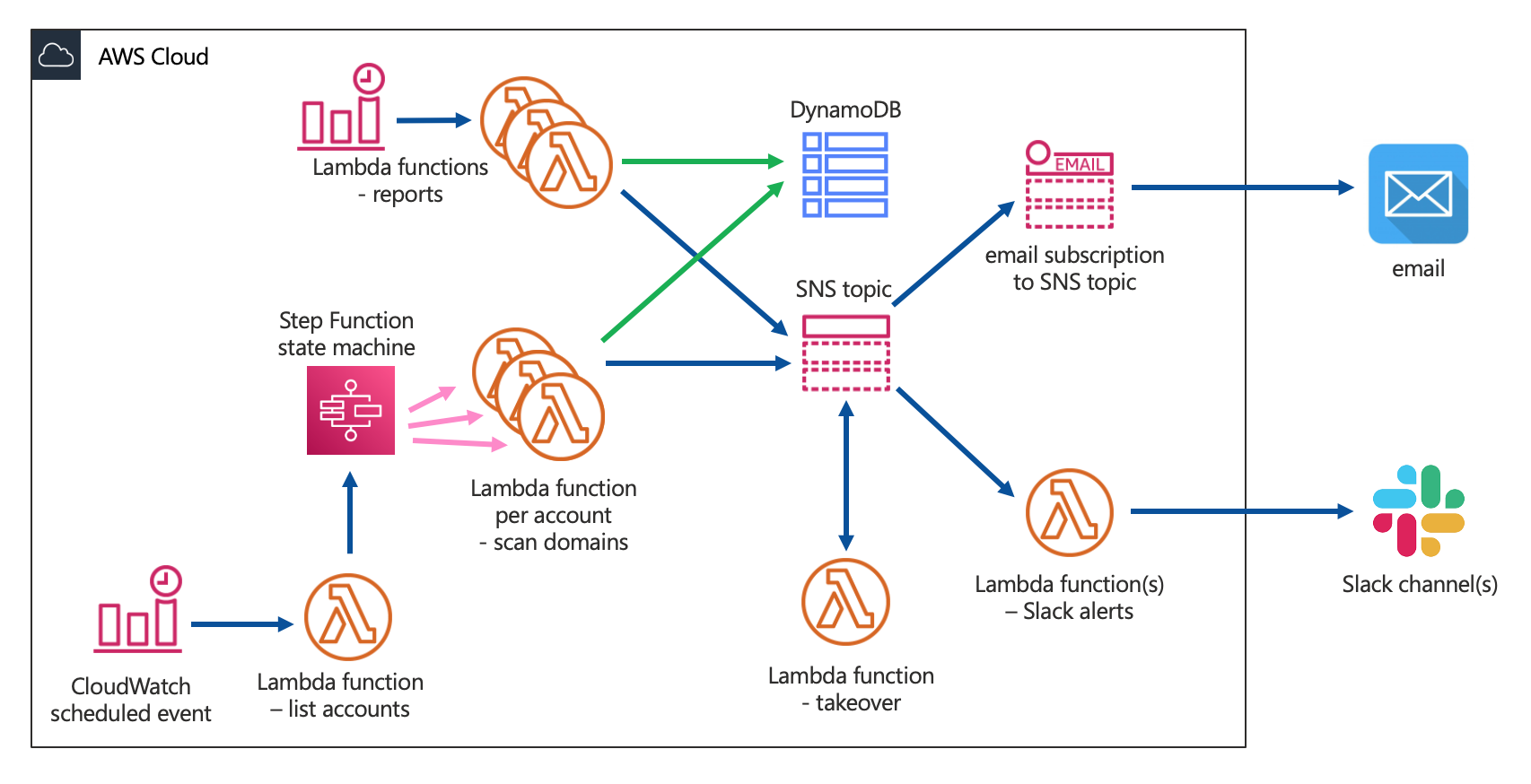
- scan Amazon Route53 across an AWS Organization for domain records vulnerable to takeover
- scan Cloudflare for vulnerable DNS records
- take over vulnerable subdomains yourself before attackers and bug bounty researchers
- automatically create known issues in Bugcrowd or HackerOne
- vulnerable domains in Google Cloud DNS can be detected by Domain Protect for GCP
- manual scans of cloud accounts with no installation
- Domain Protect is packaged as a public Terraform Module
- Ensure requirements are met
- See Installation for details on how to install
See migration for a guide to migrating from the original Domain Protect repository to the Terraform Module
📢 We welcome contributions! Please see the OWASP Domain Protect website for more details.
📄 Detailed documentation is on our Docs site
This tool cannot guarantee 100% protection against subdomain takeovers.
| Name | Version |
|---|---|
| terraform | > 1 |
| archive | > 2.2.0 |
| aws | > 5.12.0 |
| null | > 3.1.0 |
| random | > 3.1.0 |
No providers.
| Name | Source | Version |
|---|---|---|
| accounts_event | ./modules/cloudwatch | n/a |
| accounts_event_ips | ./modules/cloudwatch | n/a |
| accounts_role | ./modules/iam | n/a |
| accounts_role_ips | ./modules/iam | n/a |
| cloudflare_event | ./modules/cloudwatch | n/a |
| cloudwatch_event | ./modules/cloudwatch | n/a |
| dynamodb | ./modules/dynamodb | n/a |
| dynamodb_ips | ./modules/dynamodb-ips | n/a |
| kms | ./modules/kms | n/a |
| lambda | ./modules/lambda | n/a |
| lambda_accounts | ./modules/lambda-accounts | n/a |
| lambda_accounts_ips | ./modules/lambda-accounts | n/a |
| lambda_cloudflare | ./modules/lambda-cloudflare | n/a |
| lambda_resources | ./modules/lambda-resources | n/a |
| lambda_role | ./modules/iam | n/a |
| lambda_role_ips | ./modules/iam | n/a |
| lambda_scan | ./modules/lambda-scan | n/a |
| lambda_scan_ips | ./modules/lambda-scan-ips | n/a |
| lambda_slack | ./modules/lambda-slack | n/a |
| lambda_takeover | ./modules/lambda-takeover | n/a |
| lamdba_stats | ./modules/lambda-stats | n/a |
| resources_event | ./modules/cloudwatch | n/a |
| resources_role | ./modules/iam | n/a |
| sns | ./modules/sns | n/a |
| sns_dead_letter_queue | ./modules/sns | n/a |
| step_function | ./modules/step-function | n/a |
| step_function_ips | ./modules/step-function | n/a |
| step_function_role | ./modules/iam | n/a |
| takeover_role | ./modules/iam | n/a |
No resources.
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| allowed_regions | If SCPs block certain regions across all accounts, optionally replace with string formatted list of allowed regions | string |
"['all']" |
no |
| bugcrowd | Set to enabled for Bugcrowd integration | string |
"disabled" |
no |
| bugcrowd_api_key | Bugcrowd API token | string |
"" |
no |
| bugcrowd_email | Email address of Bugcrowd researcher service account | string |
"" |
no |
| bugcrowd_state | State in which issue is created, e.g. new, triaged, unresolved, resolved | string |
"unresolved" |
no |
| cf_api_key | Cloudflare API token | string |
"" |
no |
| cloudflare | Set to true to enable CloudFlare | bool |
false |
no |
| cloudflare_lambdas | list of names of Lambda files in the lambda-cloudflare/code folder | list(any) |
[ |
no |
| environment | Environment deploying to, defaults to terraform.workspace - optionally enter in tfvars file | string |
"" |
no |
| external_id | external ID for security audit role to be defined in tvars file. Leave empty if not configured | string |
"" |
no |
| hackerone | Set to enabled for HackerOne integration | string |
"disabled" |
no |
| hackerone_api_token | HackerOne API token | string |
"" |
no |
| ip_address | Set to true to enable A record checks using IP address scans | bool |
false |
no |
| ip_scan_schedule | schedule for IP address scanning used in A record checks | string |
"24 hours" |
no |
| ip_time_limit | maximum time in hours since IP last detected, before considering IP as no longer belonging to organisation | string |
"48" |
no |
| lambdas | list of names of Lambda files in the lambda/code folder | list(any) |
[ |
no |
| memory_size | Memory allocation for scanning Lambda functions | number |
128 |
no |
| memory_size_slack | Memory allocation for Slack Lambda functions | number |
128 |
no |
| org_primary_account | The AWS account number of the organization primary account | string |
n/a | yes |
| permissions_boundary_arn | permissions boundary ARN to attach to every IAM role | string |
null |
no |
| platform | Python platform used for install of Regex and other libraries | string |
"manylinux2014_x86_64" |
no |
| production_environment | Name of production environment - takeover is only turned on in this environment | string |
"" |
no |
| production_workspace | Deprecated, use production_environment. Will be removed in a future release | string |
"prd" |
no |
| project | abbreviation for the project, forms first part of resource names | string |
"domain-protect" |
no |
| rcu | DynamoDB Read Capacity Units for vulnerability database | number |
3 |
no |
| region | AWS region to deploy Lambda functions | string |
"eu-west-1" |
no |
| reports_schedule | schedule for running reports, e.g. 24 hours. Irrespective of setting, you will be immediately notified of new vulnerabilities | string |
"24 hours" |
no |
| runtime | Lambda language runtime. Defaults to the .python-version in repo and can be overridden. |
string |
"" |
no |
| scan_schedule | schedule for running domain-protect scans, e.g. 24 hours | string |
"24 hours" |
no |
| security_audit_role_name | security audit role name which needs to be the same in all AWS accounts | string |
"domain-protect-audit" |
no |
| slack_channels | List of Slack Channels - enter in tfvars file | list(string) |
[] |
no |
| slack_emoji | Slack emoji | string |
":warning:" |
no |
| slack_fix_emoji | Slack fix emoji | string |
":white_check_mark:" |
no |
| slack_new_emoji | Slack emoji for new vulnerability | string |
":octagonal_sign:" |
no |
| slack_username | Slack username appearing in the from field in the Slack message | string |
"Domain Protect" |
no |
| slack_webhook_type | Slack webhook type, can be legacy or app | string |
"legacy" |
no |
| slack_webhook_urls | List of Slack webhook URLs, in the same order as the slack_channels list - enter in tfvars file | list(string) |
[] |
no |
| stats_schedule | Cron schedule for the stats message | string |
"cron(0 9 1 * ? *)" |
no |
| takeover | Create supported resource types to prevent malicious subdomain takeover | bool |
false |
no |
| update_lambdas | list of Cloudflare Lambda functions updating vulnerability status | list(any) |
[ |
no |
| update_schedule | schedule for running domain-protect update function, e.g. 24 hours | string |
"24 hours" |
no |
| vpc_config | Provide this to allow your function to access your VPC (if both 'subnet_ids' and 'security_group_ids' are empty then vpc_config is considered to be empty or unset, see https://docs.aws.amazon.com/lambda/latest/dg/vpc.html for details). |
object({ |
null |
no |
| wcu | DynamoDB Write Capacity Units for vulnerability database | number |
2 |
no |
| Name | Description |
|---|---|
| accounts_event | Outputs of module.accounts_event |
| accounts_event_ips | Outputs of module.accounts_event_ips |
| accounts_role | Outputs of module.accounts_role |
| accounts_role_ips | Outputs of module.accounts_role_ips |
| cloudflare_event | Outputs of module.cloudflare_event |
| cloudwatch_event | Outputs of module.cloudwatch_event |
| dynamodb | Outputs of module.dynamodb |
| dynamodb_ips | Outputs of module.dynamodb_ips |
| kms | Outputs of module.kms |
| lambda | Outputs of module.lambda |
| lambda_accounts | Outputs of module.lambda_accounts |
| lambda_accounts_ips | Outputs of module.lambda_accounts_ips |
| lambda_cloudflare | Outputs of module.lambda_cloudflare |
| lambda_resources | Outputs of module.lambda_resources |
| lambda_role | Outputs of module.lambda_role |
| lambda_role_ips | Outputs of module.lambda_role_ips |
| lambda_scan | Outputs of module.lambda_scan |
| lambda_scan_ips | Outputs of module.lambda_scan_ips |
| lambda_slack | Outputs of module.lambda_slack |
| lambda_takeover | Outputs of module.lambda_takeover |
| lamdba_stats | Outputs of module.lamdba_stats |
| resources_event | Outputs of module.resources_event |
| resources_role | Outputs of module.resources_role |
| sns | Outputs of module.sns |
| sns_dead_letter_queue | Outputs of module.sns_dead_letter_queue |
| step_function | Outputs of module.step_function |
| step_function_ips | Outputs of module.step_function_ips |
| step_function_role | Outputs of module.step_function_role |
| takeover_role | Outputs of module.takeover_role |